Welcome back to Nightmare on VPN street with TMG and SSTP – Part 4 of 4. If you’ve been following along, we’re going to use the client to determine the SHA256 value since this isn’t “visible” within the certificate itself. Then we’ll tackle the subsequent TMG configuration and the testing.
If you want to go back to Part 3, Part 2, or Part 1, click respectively.
Here goes:
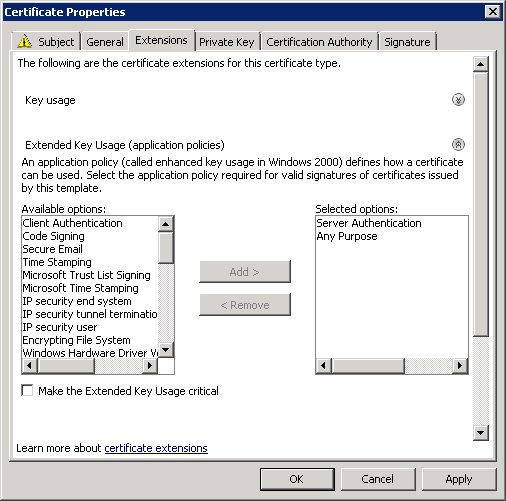
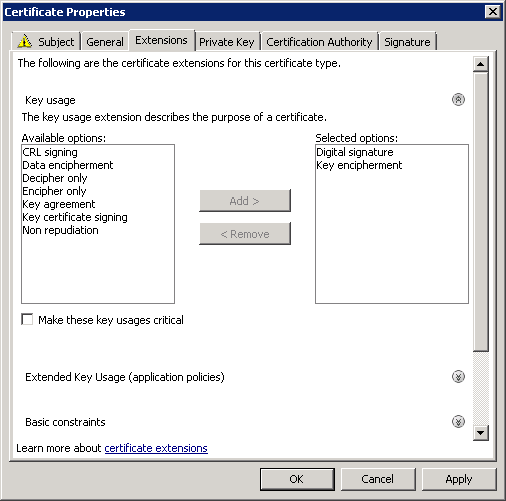
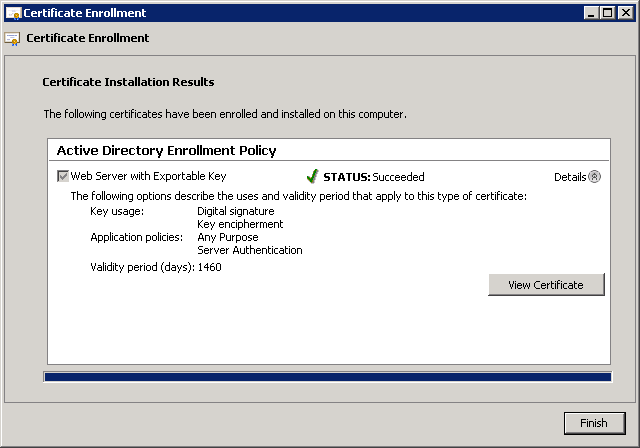
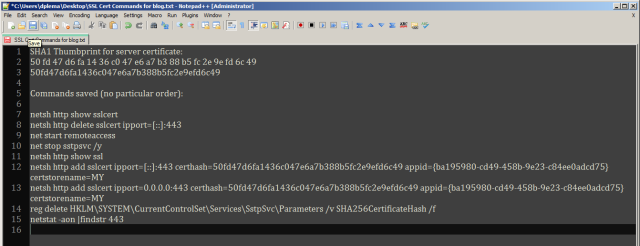
We should be at the point of being able to connect (and then immediately disconnect unfortunately) with SSTP. The configuration of my client was straight forward with only a few minor tweaks. If it was working previously, you need to change NOTHING. Oh, and before I show them to you, make sure you’ve disabled (or more accurately, ENABLED) the NoCertRevocationCheck reg key. I’ve included the config here for completeness:
- Open the Network Sharing Center control panel.
- Select “Set up a new connection or network”.
- Choose “Connect to a workplace”
- Choose Use my Internet Connection (VPN)
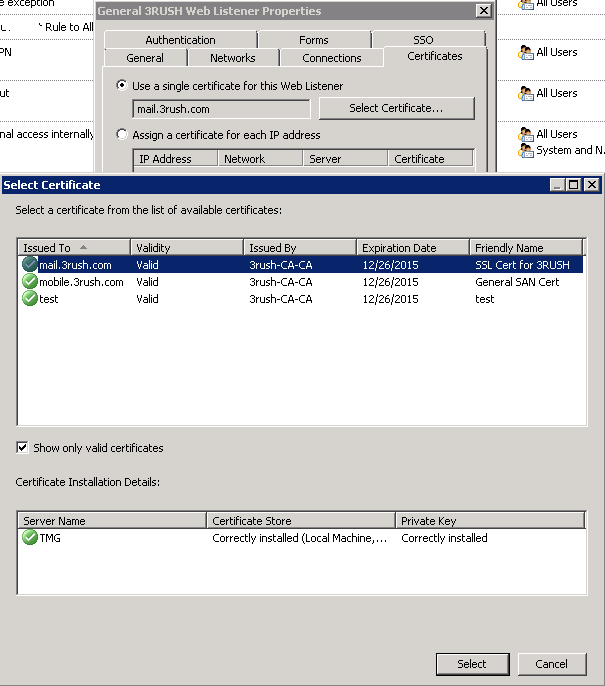
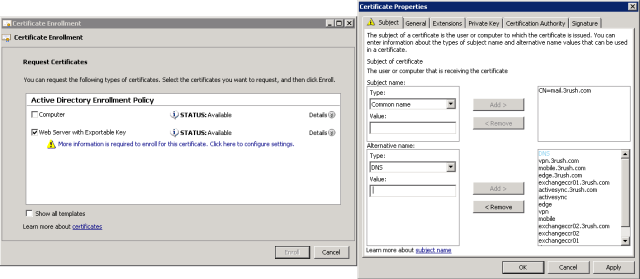
- Put it the name of your TMG server’s external presence, which should be your certificate’s SUBJECT name, e.g. vpn.domain.com
- Note, if you use the IP Address, you’ll get SSL errors, although might still be able to connect.
- Select the “Don’t connect now…” checkbox. Click Next
- Put in your credentials and click “Create” then click “Close”. If you see “connect”, then you didn’t check the ‘Don’t connect now” checkbox. Either way, it’s no big deal.
- Go back to the propertes of the connection you just created.
- Under the Security tab, change the “Type of VPN” to SSTP and then click OK. This will allow the connection to happen faster instead of RRAS trying PPTP first, timeout, try L2TP second, timeout, before trying SSTP.
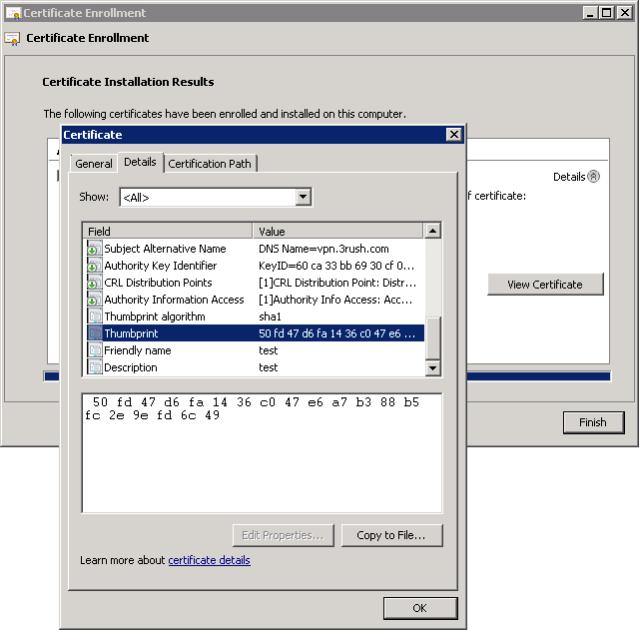
Now, here’s where we “find” the SHA256 hash value.
- Double click the VPN connection you just created and click connect – you should see it trying to connect, authenticate, then really connect – then almost immediately disconnect. Click ok.
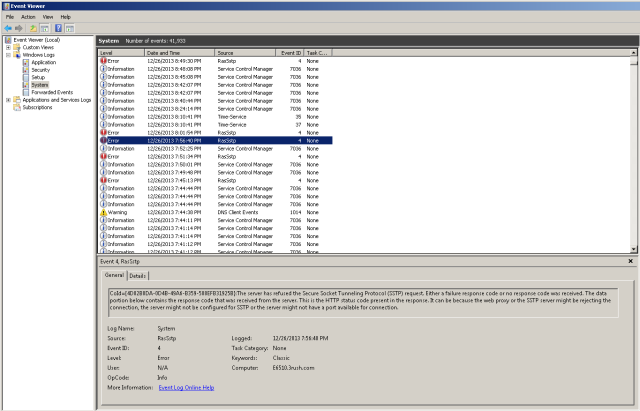
- Now, open Eventvwr on the client and look for this error Event ID 6 – RrasSstp
Note: I blacked out most of the key for security, but left you the ‘view’ so you know what to look for.
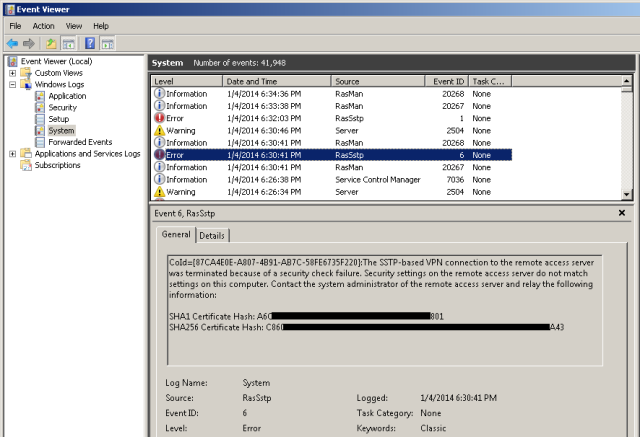
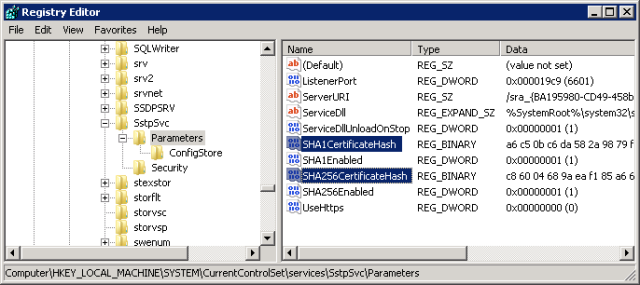
- OK, so what you’re seeing in the eventvwr is the SHA256 value that is the ACTUAL CORRECT value. We’re going to take this value and change the DUMMY SHA256 value that is in the registry on the TMG 2010 server.
- You can either manually do it using regedit, or use the command line like this:
- reg delete HKLM\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA256CertificateHash /f
- reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\SstpSvc\Parameters /v SHA256CertificateHash /t REG_BINARY /d this_is_the_SHA256_hash_value_you_copied_from_the_eventlog_on_the_client /f
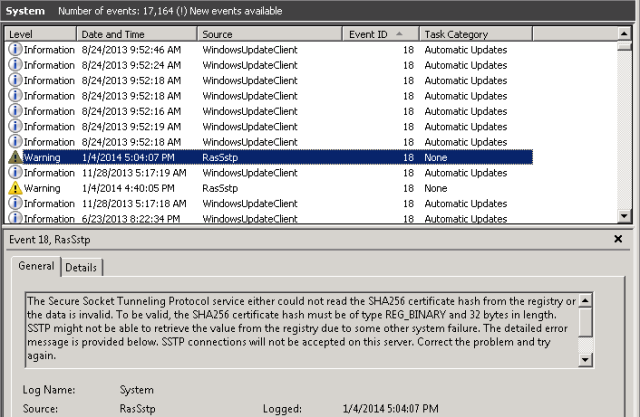
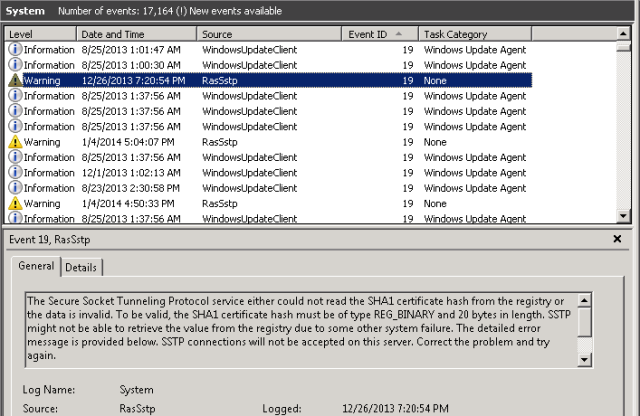
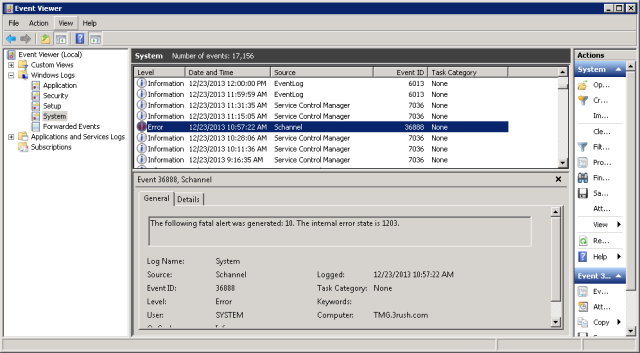
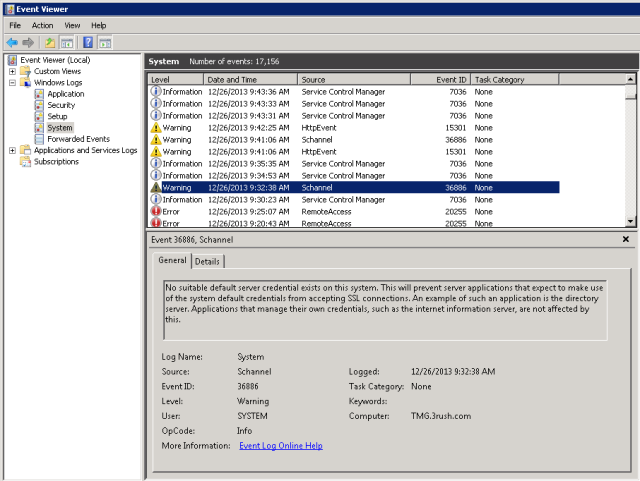
At this point, I recommend rebooting the TMG server and making sure everything comes back relatively clean. You should no longer see the Schannel errors nor the RRAS SSTP Event ID errors 18 or 19 since the hashes are now correct in the registry for SHA1 and SHA256.
Now you should be able to connect from your client using the SSTP VPN connection and STAY connected.
I hope this helps anyone out there save some time with it comes to replacing computer certificates on TMG 2010!